ICT Policy Review Guide Generator
Is this tool helpful?
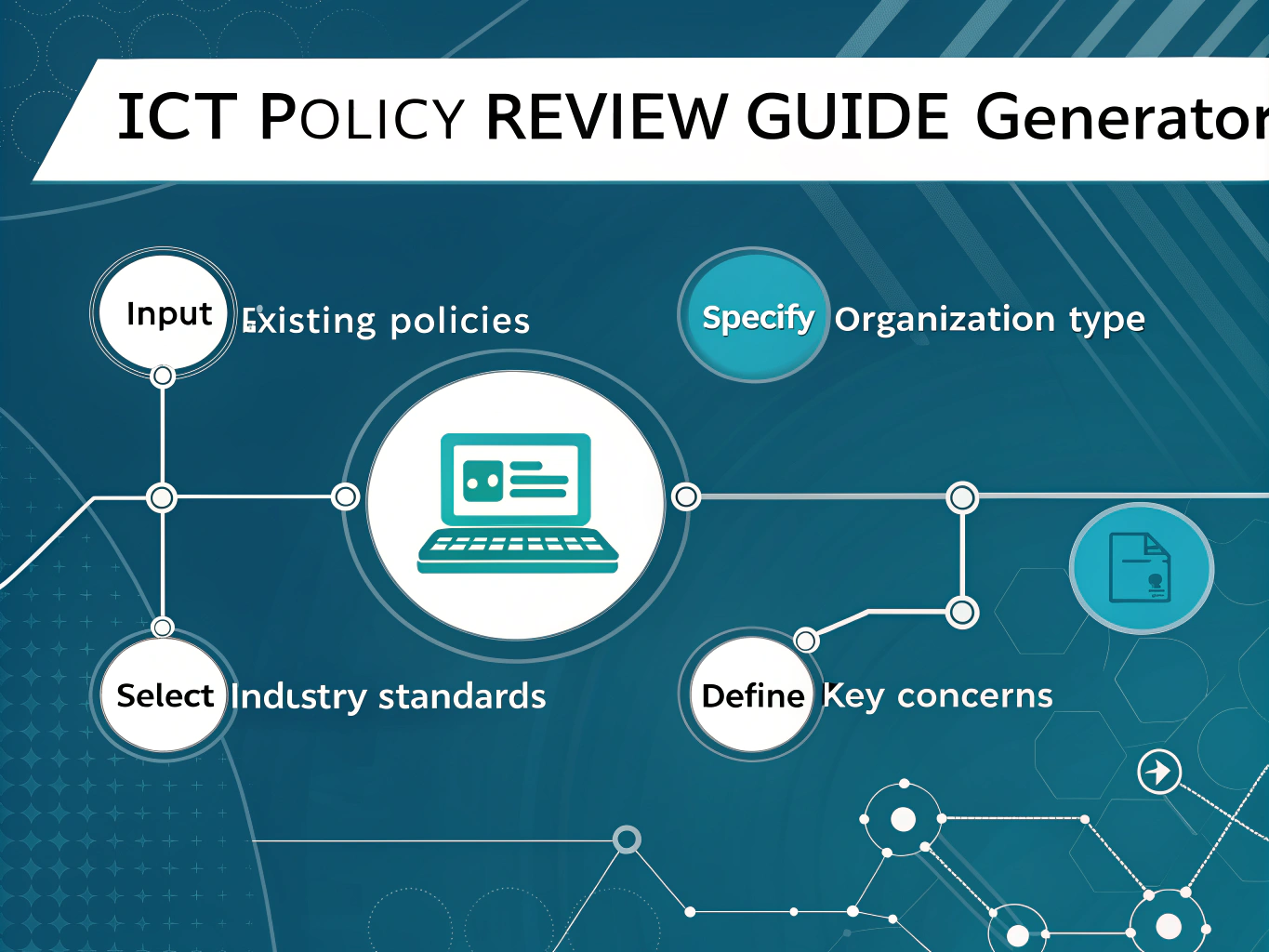
How to Use the ICT Policy Review Guide Generator Effectively
Follow these steps to get the most accurate and tailored ICT policy review guide for your organization:
- Existing Policies (Optional): Provide a brief summary of your current ICT policies and procedures. For example, you could enter, “We maintain a comprehensive IT asset management system and employee internet usage guidelines.” or “Our firm follows a disaster recovery plan established in 2019 with annual updates.”
- Organization Type: Specify your organization’s category to customize the review process. Examples include “Public university” or “Small retail business.” This helps the tool target relevant policy considerations.
- Industry Standards (Optional): List any applicable regulations or frameworks your organization follows. You might input “SOX, FISMA” for financial institutions or “FedRAMP, NIST” for government contractors.
- Key Concerns: Outline the main topics you want your ICT policy review guide to address. For instance, “Mobile device management, cloud data security, and incident response” or “Software licensing compliance and internal audit procedures.”
After entering all necessary details, click Generate ICT Policy Review Guide. The tool analyzes your input and delivers a personalized guide that helps you review and improve your ICT policies efficiently.
Introduction to the ICT Policy Review Guide Generator
The ICT Policy Review Guide Generator is a practical tool designed to help organizations evaluate and strengthen their Information and Communications Technology policies. By leveraging your inputs, it generates a customized roadmap for reviewing your ICT policies according to your organizational context and relevant industry standards.
Purpose and Key Benefits
This tool simplifies the ICT policy review process, which can often feel overwhelming and technical. It helps you:
- Align your policies with up-to-date industry regulations and best practices
- Identify gaps or outdated areas in your current ICT policies
- Adapt policies to emerging technology trends and organizational changes
- Improve cybersecurity measures and operational efficiency
- Establish clear, well-structured guidelines that are easy to follow
Practical Applications of the ICT Policy Review Guide Generator
Different organizations use this tool to meet their unique ICT governance challenges. Below are some common scenarios:
1. Small Non-Profit Preparing for Data Compliance
- Organization Type: Regional non-profit organization
- Key Concerns: Data handling standards, volunteer access controls, cloud storage policies
The guide helps this non-profit update policies to protect donor information and comply with data privacy laws tailored to their operations.
2. Educational Institution Enhancing Cybersecurity
- Organization Type: Community college
- Industry Standards: FERPA, NIST Cybersecurity Framework
- Key Concerns: Student record privacy, network access controls, remote learning security
The tool creates an actionable review guide to improve the college’s cybersecurity policies supporting both on-campus and remote students.
3. Technology Firm Ensuring Global Policy Consistency
- Organization Type: International software developer
- Industry Standards: GDPR, ISO 27001
- Key Concerns: Data localization, access management, incident reporting procedures
The generated guide assists the firm in standardizing ICT policy reviews across multiple offices while meeting varying legal requirements.
Key Features and Benefits of Using This ICT Policy Review Tool
Fast and Resource-Efficient Policy Review
The tool saves you time by providing a ready-made review roadmap. Instead of researching extensively, you get targeted advice and action steps tailored to your organization.
Tailored Customization Based on Your Inputs
By asking for your organization type, existing policies, and key concerns, the tool customizes the guide to your specific needs, making the outcomes more relevant and actionable.
Compliance with Industry Regulations
Inputting relevant industry standards ensures your policy review aligns with current legal and regulatory frameworks, helping you stay compliant and avoid penalties.
Comprehensive Policy Evaluation
The guide covers important aspects such as:
- Reviewing and updating existing ICT policies
- Identifying outdated or missing policy components
- Incorporating new technologies and cybersecurity practices
- Structuring policy documents for clarity and accessibility
- Implementing policy changes with effective organizational engagement
Encourages Ongoing Improvement
Using the tool regularly helps build a culture of continuous ICT governance improvement, keeping your policies relevant in an ever-changing technological and regulatory environment.
Common Challenges Addressed by This ICT Policy Review Guide Generator
Bridging Expertise Gaps
For organizations without dedicated ICT policy experts, the tool provides expert-level guidance on best practices and compliance requirements.
Keeping Policies Current with Technology Changes
It prompts you to consider new technologies, allowing your policies to evolve alongside technological advances such as cloud computing, mobile work, and cybersecurity threats.
Simplifying Regulatory Compliance
The tool helps you identify and incorporate the right regulations based on your industry, reducing the complexity of compliance management.
Streamlining Policy Structure and Consistency
It offers formatting and structuring tips to make your ICT policies clear, consistent, and easy to understand for all stakeholders.
Facilitating Implementation
The generated guide includes practical strategies to engage your organization, manage approvals, and roll out policy changes effectively.
Important Disclaimer
The calculations, results, and content provided by our tools are not guaranteed to be accurate, complete, or reliable. Users are responsible for verifying and interpreting the results. Our content and tools may contain errors, biases, or inconsistencies. Do not enter personal data, sensitive information, or personally identifiable information in our web forms or tools. Such data entry violates our terms of service and may result in unauthorized disclosure to third parties. We reserve the right to save inputs and outputs from our tools for the purposes of error debugging, bias identification, and performance improvement. External companies providing AI models used in our tools may also save and process data in accordance with their own policies. By using our tools, you consent to this data collection and processing. We reserve the right to limit the usage of our tools based on current usability factors.